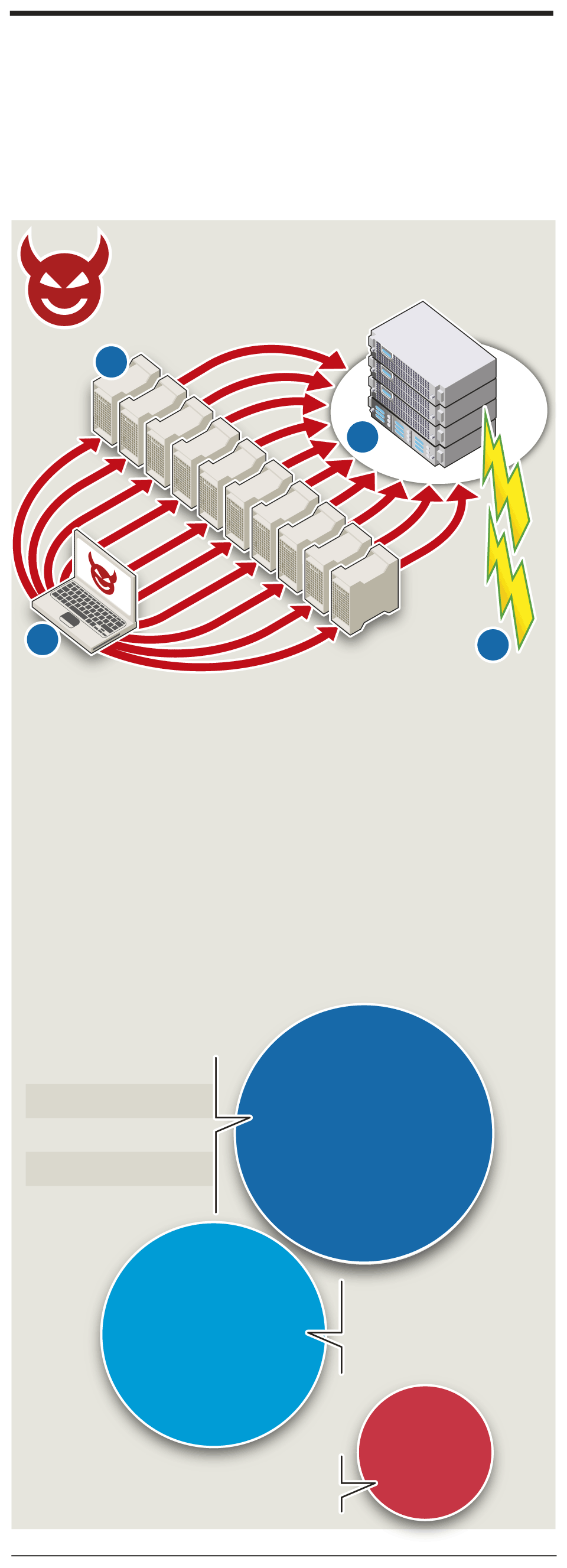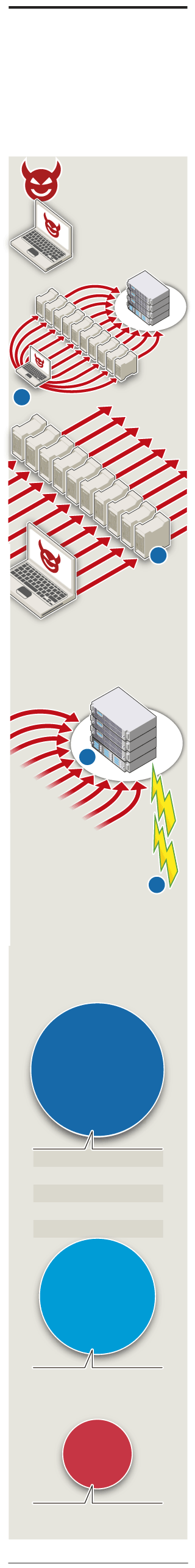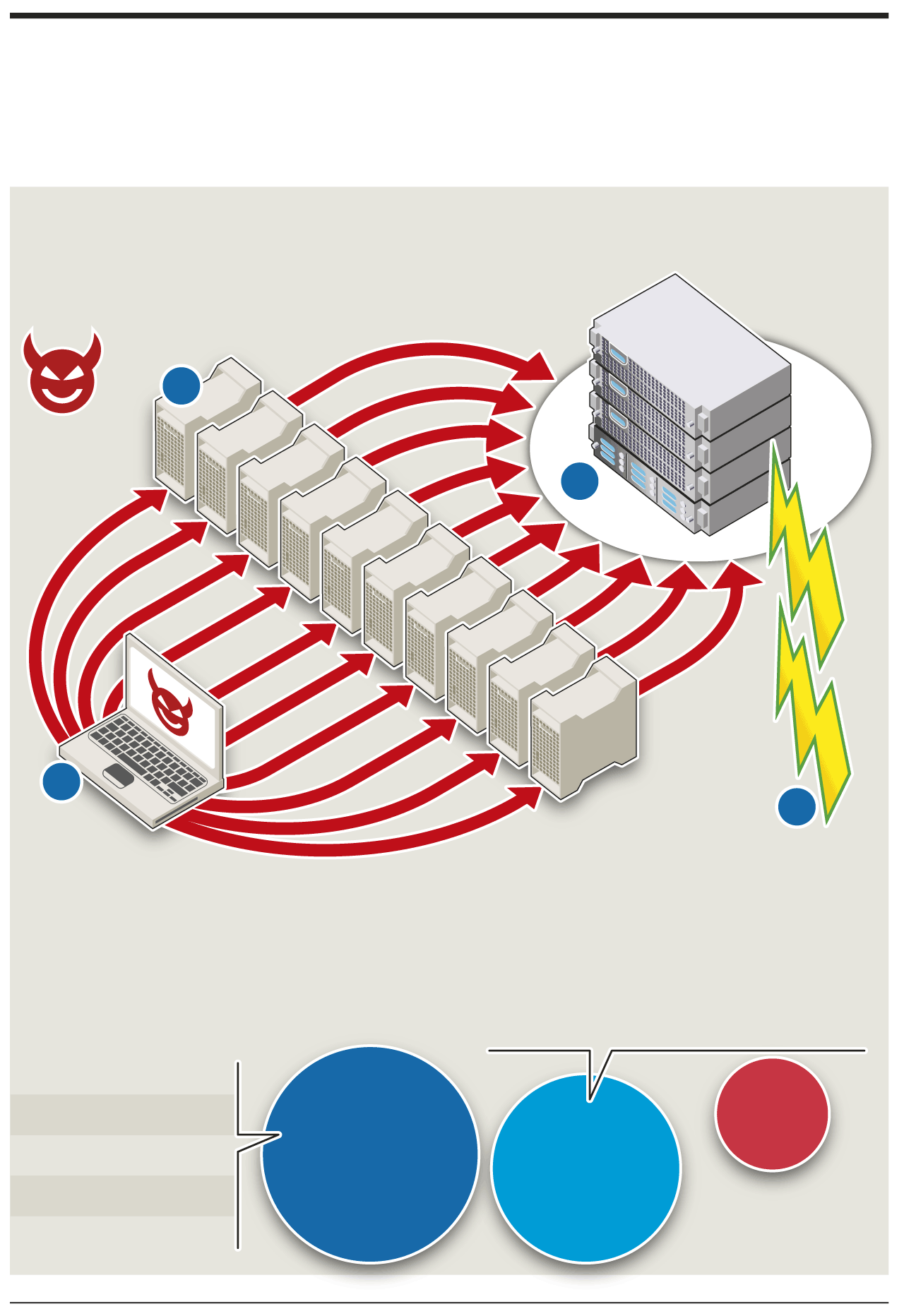
Cyber smokescreen to steal data
Distributed denial-of-service (DDoS) assaults – which overwhelm an online service with fake requests – are increasingly being used to mask attacks to steal sensitive information from a company
Launches DDoS
Large clusters of cellphones,
1. Attacker:
2. Botnets:
assault to exhaust server
resources (memory) and
clog “pipelines” to network
PCs or routers, infected with malware,
allow remote control
by hacker
Victim
company
2
3
1
4
Attacker
Malicious code, such as
4. Attack:
DDoS assault does not
3. Firewall:
SQL-injection,
tells database
breach security perimeter but forces
IT team to mitigate damage, masking
real attack
server to bypass authentication
and retrieve customers’ bank and
credit card details
DDoS attacks detected
74%
of DDoS attacks are
(Oct 1-7, top five countries affected)
smokescreens for other attacks…
U.S.
Russia
France
India
Germany
256,212
211,948
118,670
34,809
30,732
126,516
652,371
482,754
DDoS attacks
in seven
days
other
attacks
26%
…of which
are sensitive
data theft
Source: Kaspersky Lab Denial of Service report
© GRAPHIC NEWS